SIEM as a Service
Security Information and Event Management (SIEM) is a solution that combines and examines activity from different resources across the entire Information Technology infrastructure. It collects data from other network devices and servers. It helps to detect threats and alert the organization. Security information and event management (SIEM as a Service) is an approach that acts as a lookout over the information security of the organization. It aims to reunite log data from different users and servers and then evaluate if there are any security threats. It also helps to take an immediate step for eradicating risk.
We need to also gather some information, how it works.
Let’s Understand the SIEM Process?
SIEM piles up logs and events from various sources of the organization. Each device of the organization generates an event. The SIEM collects data from different sources around. It tries to collect data from an agent installed on the device. This is the most common source of collecting data. It can also connect directly to the devices using an API call or network protocol. It can also access log files directly from storage. It follows the Syslog format. One another way of collecting data through a protocol that streams an event. Examples of such protocols are as follows- SNMP, Net flow, or IPFIX. The SIEM as a Service collects data and saves it in a format that makes analyzing such data easy.
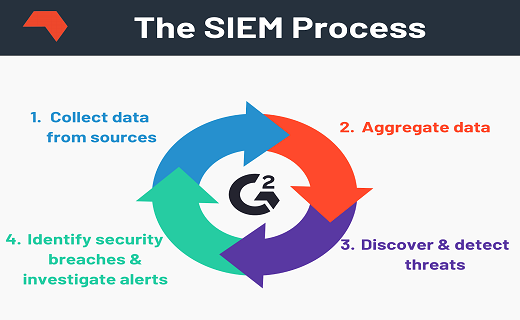
Steps to be followed in SIEM Process
The SIEM process is very simple. The whole process covers four stages mainly. They are as follows-
- The first stage is collecting data from various sources around.
- It then combines all such collected data.
- In the next process, it starts examining the data to discover threats.
- Identifies security breaches and alerts organizations about such threats.
While carrying out the process of SIEM as a Service we need to deploy things properly. We need to question ourselves a few things before beginning the process of SIEM.
- We need to answer first where we will implement SIEM. We also need to identify the databases, digital assets, and network areas which need supervision and early detection of threat. We also need to know the full coverage of our network.
- Are we planning to implement SIEM at a single stroke? Instead, we are planning to implement it on the criteria of location, slowly and carefully.
- Do we have a good security team? They will be monitoring the process of SIEM. It requires continuous attention and examination of data to function perfectly.
- We also need to identify and understand the issue to be tagged for which we need a solution.
Once you are answered with the question, you might find it necessary to keep two separate SIEM. It will help you to achieve the most desirable result. Sometimes it can be very noisy. Thus, we can prefer one for data security and others for compliance.
An organization uses SIEM as a Service for the multi-task. Its primary function is log management. But few of them also use it for complying with various regulations like HIPPA, PCI, SOX, and GDPR. Right from aggregating data to tracking data over time can be done. It also helps in tracking the growth of the organization. It can also be used as a tool for budgeting.
For the successful implementation of the SIEM process, we need to have an active security team in our organization. It also requires the involvement of the whole workforce of an organization. The employees are the backbone of an organization. They play an important role in carrying out any function of the organization. The employed should give an eye and function quickly. They can identify the attack immediately and any suspicious party in the world of digital gadgets.
Well, your organization should have three team members for the successful implementation of the SIEM process. The teams are as follows-
- Security team- A team should be formed to work actively. They are known as security personnel. They will circulate all the information and alerts. This will help the organization to take steps against online threats.
- Operation team- They will operate online. They will examine the logs, events, and other security incidents. This will provide them a quicker solution for all such problems.
- Compliance team- They are an important team for the organization. They will handle the data. They will also compile with the rules of industry and government rules.
Whether to take care of IT infrastructure or financial information of an organization, implementing the SIEM process is very much crucial. It will prevent malware attacks and provide immediate assistance.
What are three characteristics of SIEM?
Related Resource