Mobile Device
Manager
A seamless setup process allows users to instantly enroll their devices in MDM as soon as they power on their mobile devices. Easy-to-follow mobile policy guidelines address privacy concerns.
MOBILE DEVICE MANAGER:
FRICTIONLESS
DEVICE SECURITY ENROLLMENTS
- Streamline Device Enrollment
- Add and Manage BYOD
- Enforce Security Compliance
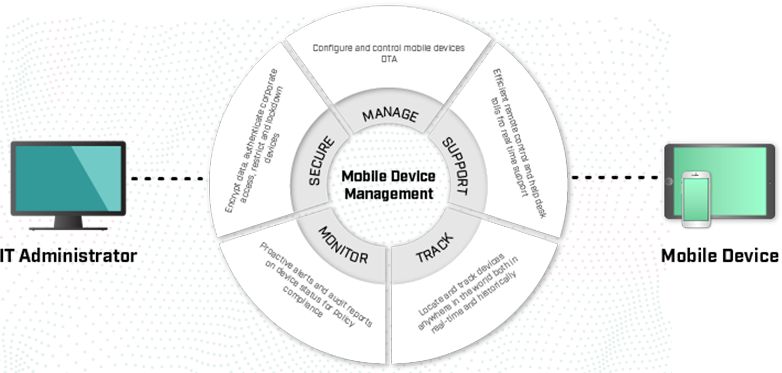
Apply Security, Settings, and Control
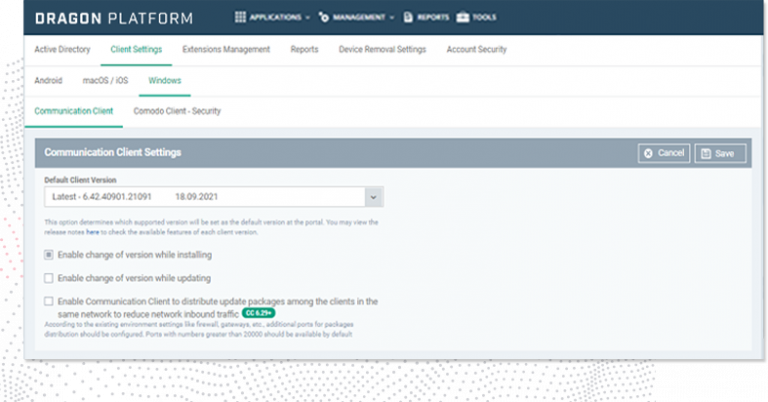
Comodo’s mobile device management allows users to enroll their devices as soon as they power them on, and a self-service portal allows them to manage common tasks, such as adding or retiring devices, without IT assistance. Registered devices are automatically configured with corporate connectivity settings, email profiles, and device-specific restrictions, which reduces help-desk calls.
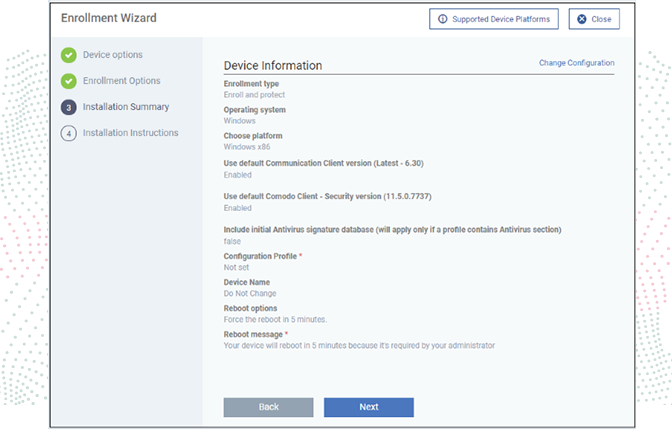
Connect Devices without Custom Rules
New employees, consultants, and third parties bring their own devices but your IT team will need to grant access to your sensitive data and files to conduct business. Setup your security policies and network on their devices quickly with the least amount of downtime and resources. Deploy, retire, secure, monitor, and manage new or BYOD mobile devices with GPS location, wipe, and device encryption in minutes, not days.
Your Network, Your Settings Any Device
Comodo’s MDM allows your IT team to identity and access management leveraging existing identity stores such as Active Directory, combined with support for granular policy settings, give visibility and control over devices that access sensitive information. We integrates with IT systems, including corporate directories (Active Directory/LDAP), IT service management (ITSM) software, and network access control (NAC) systems to create a mobile-aware IT infrastructure to accelerate business processes.
Bring Your Own Device Compatible
Provide access to any user’s device while reinforcing the integrity and security of your IT systems and network policies.
Automated Device Configuration
Registered devices are automatically configured with corporate connectivity settings, email profiles, and restrictions.
Device Encryption + DLP
Device encryption and data loss prevention settings protect data and help ensure compliance with regulatory guidelines.
Regulate Compliance Requirements
Meet regulatory guidelines defined by CJIS, HIPPA and PCI standards without preventing limited access on new devices.
Vault Sensitive Data
Granular policy settings and compliance configurations allow you to adapt security to match your exact business requirements.
Enforce Security Policies
An intuitive policy engine establishes helps enforce a consistent mobile device security framework for protection and compliance.