Global Threat Intelligence
Threat Intelligence: Turn Back the Clock Against cyber threats
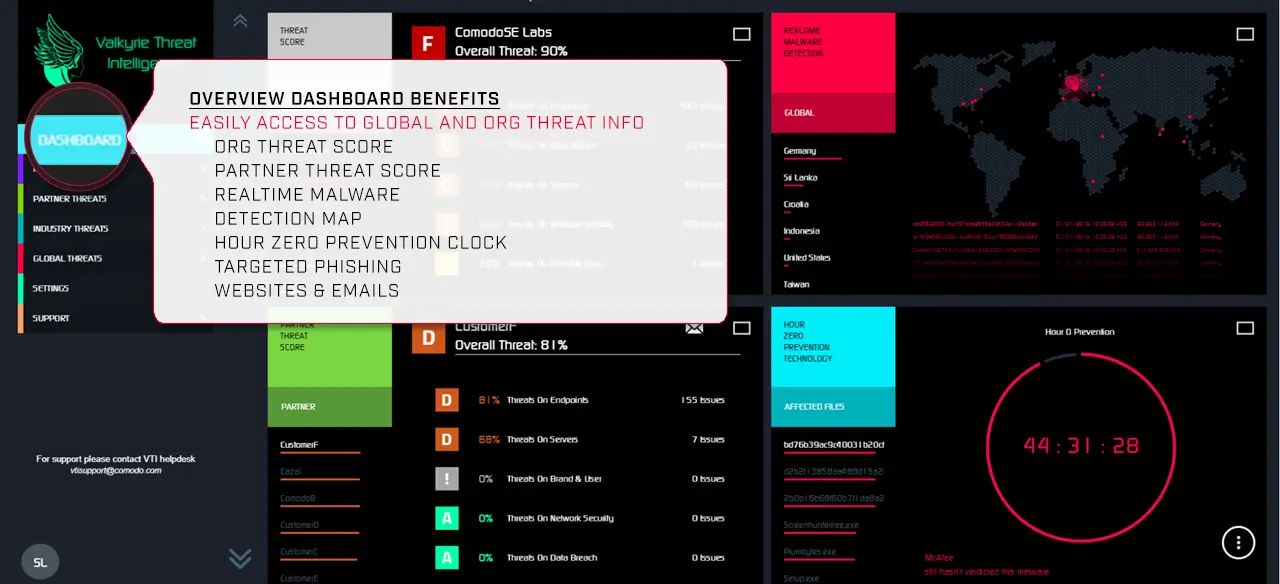
Quick verdicts are imperative for guaranteed security. And through Valkyrie Intelligence, we’ll help you eliminate your attack time surface.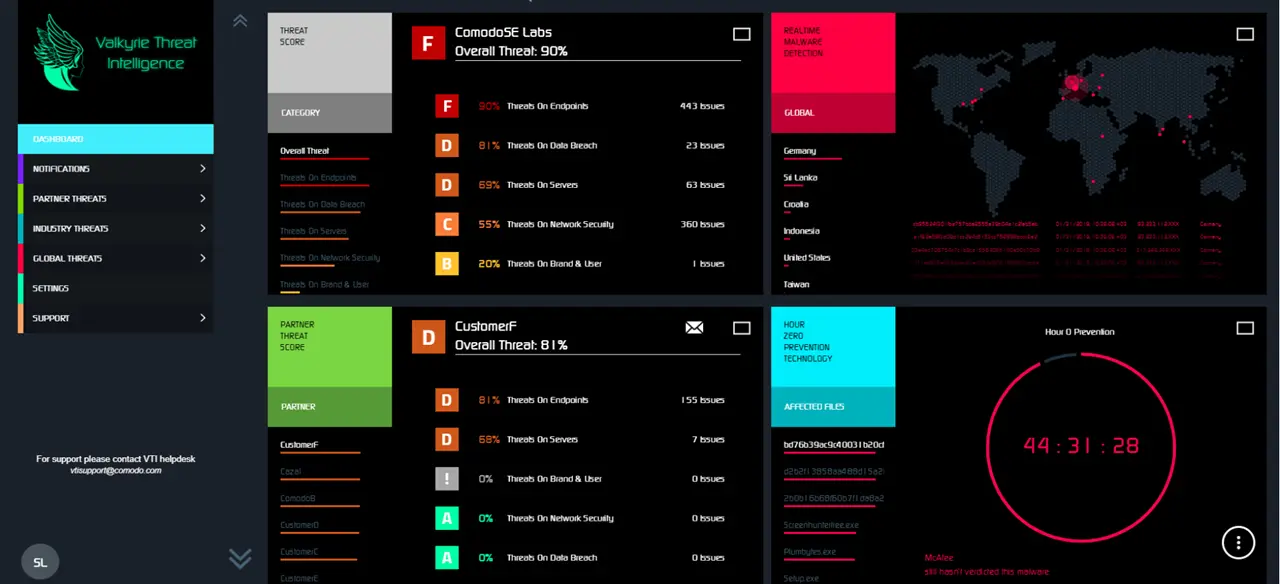
Global Threat Intelligence

Comodo’s sophisticated verdicting engine provides you insight with 100% trust on all files in your network at lightning speed
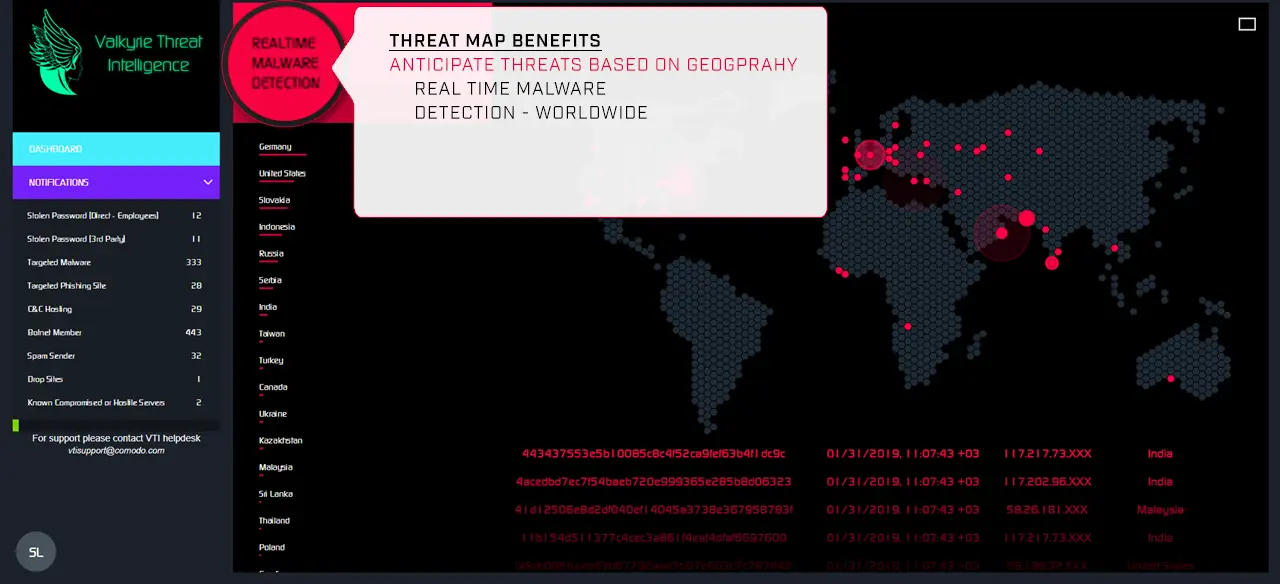
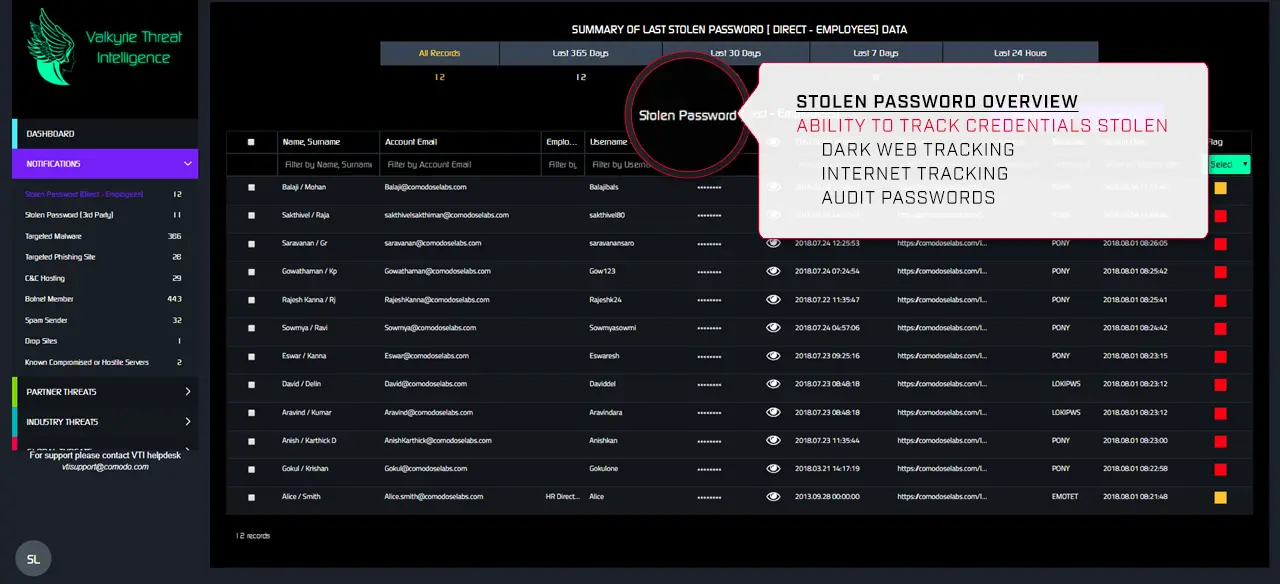
You are now leaving our web site being redirected to a third party web site operated by Sectigo Ltd.