Endpoint Manager
Practice cyber hygiene to reduce the attack surface by identifying applications, understanding the vulnerabilities and remediating patches.

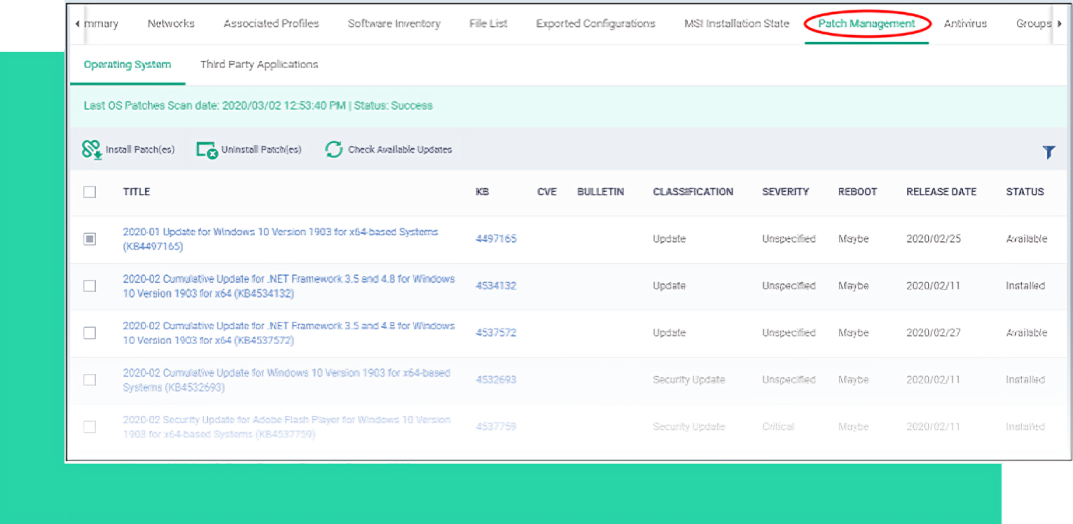
View patches needed on devices, applications, and operating systems communicating with Endpoint Manager. Consolidate time, resources and efforts by centralizing your activities into one simple to use patch management system.

Protection against zero-day web threats, without hindering employee productivity. Detect 100% of unknown fileless threats with Xcitium's intelligent file analysis engine. Apply our recommended policy, created upon a meticulous examination of threat behavior analytics.
The dashboard shows real-time data about the operating system, connection status and security posture of all devices enrolled to Endpoint Manager. The dashboard also lets you view threat results, notifications, and generate reports.

Manage your device’s operating software to ensure Linux, Windows or Mac systems are optimized, protected and secured.
Each profile lets you specify a device’s network access rights, overall security policy, antivirus scan schedule settings.
Update your devices, OS, and 3rd party applications manually or automatically through one consolidated list.
The scan will identify both managed and unmanaged devices. You can configure EM to alert you if a scan finds new devices.
Our lightweight agent to collect information and drill down into incidents with base-event-level granularity.
Create procedures and monitors to track certain activities and generate an alert if their conditions are met.
Conducts multiple arrays of run-time behavioral analysis against unknown files to provide a verdict of safe quickly and automatically or malicious.
Automatically runs from patented virtual container that does allow threats to access the host system’s resources or user data.
Push or rollback updates more efficiently with bulk installation area lets you download the communication package.
Move from Detection to Prevention With ZeroThreat to isolate infections such as ransomware & unknowns.
Learn MoreGain full context of an attack to connect the dots on how hackers are attempting to breach your network.
Learn MoreWe continuously monitor activities or policy violations providing cloud and network virtualized containment, as well as threat hunting SOC Services, and 24/7 eyes on glass threat management.
Learn More