What Is the Difference Between SIEM and IDS Systems?
With the growth of technology, there is a growth in the intensity of cyber threats. It is important to know about the latest security technology, their working, and which one will suit your business to remain protected.
SIEM and IDS are terms associated with cybersecurity. While a SIEM software i.e. security information and event management system allow features such as threat detection, incident management, compliance by collecting and analyzing the security events. IDS or intrusion detection system is a software that detects vulnerability exploits as compared to a targeted application. The prime difference between SIEM and IDS is that SIEM software is mainly for preventive action whereas IDS detects events of cyber threats and reports them.
Let us understand each system in detail and how they work together.
What is SIEM?
SIEM is a solution for cybersecurity which combines:
Security Information Management (SIM):
This works by collecting log data for further analysis, sends out alerts to the security team for threats and events.
Security Event Management (SEM):
This conducts system monitoring on a real-time basis, notifies the security team about important issues, and creates correlations between events.
The basic principles of a SIEM software are to aggregate data, find out deviations from preset rules, and suggest a proper plan of action in case of a security issue. This technology is built to improve the data security strategy of any organization. In the absence of this software, the IT staff will not have any knowledge of logs and events, so they might miss out on signs of threat.
The primary components of a SIEM system are:
- Log event management and collection.
- Can analyze events and related data from multiple sources.
- Operational capabilities such as dashboards, incident management, and reporting.
- Can take feed from threat intelligence software that is open-source.
- Security incident management and compliance.
There are multiple benefits of these components such as:
- It takes less time to identify and mitigate threats.
- The security team gets a holistic view of the InfoSec environment of the organization.
- Multiple-use cases can be designed around log and data management including compliance and audit reporting, security policies, network troubleshooting, and helpdesk.
- Security alerts and threat detection.
- Better digital forensics when a major security incident happens
What is IDS?
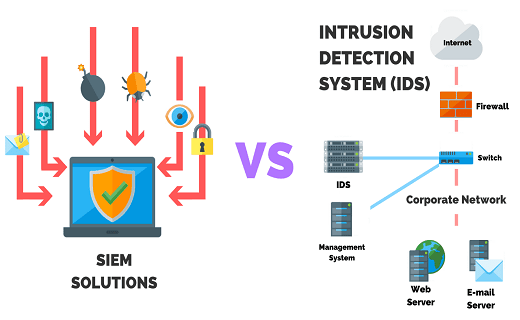
IDS can be a device or software which monitors the system or network for any policy violations or malicious activity.
The detection methods of an IDS system include:
- Signature-based detection: -Provide Strong Tag this detects attacks by checking for some patterns in your network traffic or checks for signatures of malware. Signatures are sequences of malicious instruction. They can detect known cyberattacks easily but struggle in case of novel cyber threats.
- Anomaly-based detection: -Provide Strong Tag they detect misuse and intrusions by classifying network activity as anomalous or normal. This is designed for unknown attacks by new types of malware. The software uses machine learning to define a trustworthy event and compares it to the event which is happening. This is better than signature-based systems but there are more false detections and alarms in this case.
- Reputation-based detection: -Provide Strong Tag this software makes use of reputation scores to detect potential cyber threats.
IDS systems can be grouped into two types namely:
Network intrusion detection system (NIDS):
These are kept at strategic points in the network to check the network traffic from and to the device. The passing traffic is analyzed based on a library of known attacks. In case of identification of an attack, a notification is sent to the security team.
A host-based intrusion detection system (HIDS):
Monitors and runs important files on one device or host. IT works by monitoring the outbound and inbound packets from the device and then sends alerts to the user in case of detection of suspicious activity. Snapshots of existing files are taken and then matched with previous ones to see if critical files have been deleted or modified and then alerts are sent.
Working of IDS and SIEM together:
SIEM as a Service and IDS are two software that is usually used together to find and avoid unauthorized access or compromise of sensitive confidential data. Just like SIEM, the IDS system can also manage logs but it does not have the feature to centralize it and find relations between event data from multiple systems.
So, in most organizations, IDS systems are used for detection of malicious activity which is then sent as an alert to the SIEM system. From there the security team is notified and analyzes the data to check whether it is a real threat or not.
For more information about SIEM and IDS system and their co-working visit our website https://www.comodo.com/partners/mssp/
Related Resource