Today, a business's biggest challenge is protecting its endpoints- which are becoming more vulnerable to malware, trojan, ransomware, and other cyber attacks.
Example of EDR
In 2022, Cybercriminals targeted government organizations, Fortune 500 companies, factories, airlines, and many other businesses. Ransomware was the most common type of endpoint attack worldwide in 2022.
Example of EDR - The best way to protect the endpoint is to rely on Endpoint Detection and Response system. Many businesses wonder, "What is an EDR?".
If you have the same question, it's time to get a clear picture below.
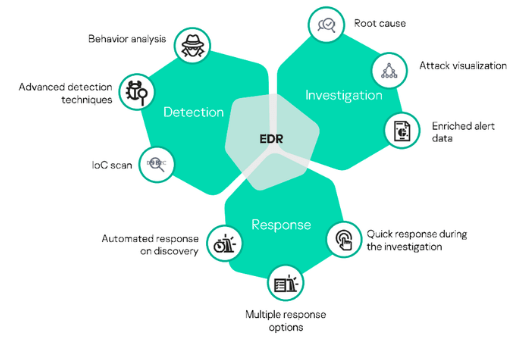
The Best Example of EDR - Xcitium
This Endpoint detection and response tool help you protect your business endpoint most efficiently. Xcitium EDR allows an organization to detect threats quickly and respond to them proactively.
Example of EDR - This EDR solution employs AI-based technologies, including machine learning and behavior analytics, to identify potential threats. It helps you look closely at all endpoints and detect malicious behavior and suspicious activities.
The security team needs some practical tools to monitor endpoints; nothing works better than Xcitium EDR. It offers incredible visibility into endpoints to detect cyber threats and protect your network against cyber-attacks and data breaches.
The big plus of using this Endpoint tool is that it works better than traditional security measures such as firewalls and antivirus. Many brand new malware is difficult to spot with antivirus, and your organization needs the most effective endpoint detection and response system like Xcitium EDR
5 Key Features of EDR
When you search the market, you can find a wide variety of examples of EDR Solutions. Here are some key features that make EDR tools effective for your business security.
1. Endpoint Data Collection
Whether you get Xcitium EDR or any other, it will collect the data from your endpoint. An agent will monitor all the endpoints devices 24 hours a day and 7 days a week. It will collect all the data and store it in a centralized hub for processing.
The best EDR agent needs to be more resource extensive. In other words, it will take a little memory and computer processing power. Fortunately, Xcitium has a lightweight agent that runs in the background and never slows down the system's performance.
2. Threat Detection and Analysis
Another function in almost every example of the EDR tool is threat detection and analysis. This tool uses artificial intelligence (AI) and machine learning (ML) technologies. Some tools also have deep learning and behavior analysis capabilities.
Once an agent collects all the data, it will analyze it using this technology so that your security team can get contextualized insight.
Xcitium EDR tools come with a threat database, so it becomes easy for your team to analyze a potential threat. It becomes easy to whitelist traffic or create some benchmark for suspicious activity.
3. Automated Response
Do you know that when you have an EDR, you don't need an antivirus? Yes, it's true; you can secure your endpoints through EDR. It will monitor endpoints and create an automatic response in case a threat is detected. It even goes one step further than an anti-malware program by alerting your security team and sharing a response workflow.
The best example of an EDR is Xcitium EDR, where a threat is blocked by a tool, and your security analyst can check the details of incidents. They can check event logs to understand a threat better.
4. Incident Investigation
An EDR can help you prevent future attacks on your system. The most important thing to manage risk is getting the threat's full context.
Example of EDR with an incredible Incident Investigation. Then undoubtedly, the best answer here is Xcitium EDR. It brings a clear threat pathway. Your security team can get an idea of how a threat started, how it impacted an endpoint, and where your endpoint was vulnerable.
This contextualized information is crucial in preventing future attacks. As soon as your security team gets all this information, they can better patch and repair vulnerabilities. It's how they make your endpoints more secure than before.
5. Compatibility
Every organization wants to get the best endpoint detection and response tool. And what makes a tool best is its compatibility. You may be running other security solutions in your business network. So, you definitely need a program that integrates well with your overall security infrastructure without causing any issues.
Try Xcitium's EDR Security Software
In other words, you need a fully compatible EDR that works closely with other security solutions. Now, if you ask me what an example of EDR with good compatibility is, then Xcitium EDR is an ideal solution. You can integrate it with your company's native solution without much effort. It's highly flexible and brings a user-friendly interface for effortless configuration
