Best Endpoint Detection Response (EDR)
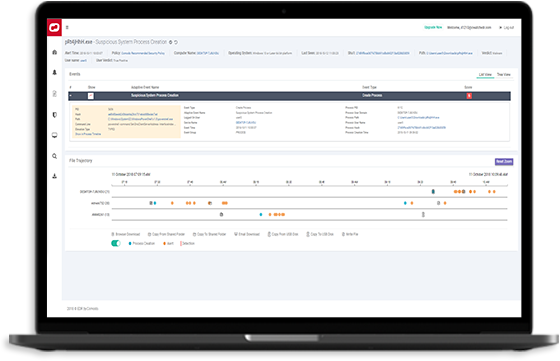
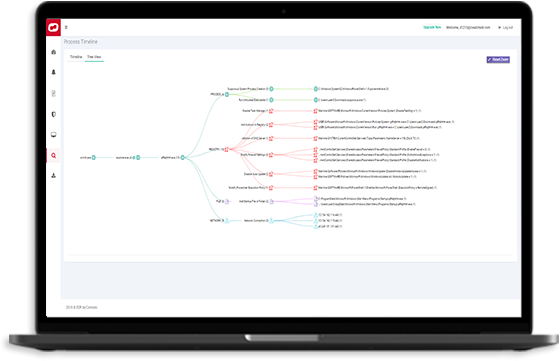
Complete Best Endpoint Detection Response with extensive threat hunting and expanded visibility
Quick verdicts are imperative for guaranteed Edr security. And through Verdict Cloud Intelligence, we’ll help you eliminate your endpoint detection EDR security attack time surface.